Avanan researchers have discovered an interesting “marketing” campaign from a legitimate company that leverages pension fund fraud tactics normally used in phishing attacks.
These phishing-like emails target the employees of U.S. municipalities, and impersonate the municipality itself, indicating a fake change in the city’s policy and then recommending the end-user sets a meeting with the pension fund.
These fraudulent emails refer to the fund as a trusted source to offer financial advice and assistance in planning for retirement, and recommends scheduling a call with an expert from this fund.
This is not a phishing attack; rather it is phishing tactics used by a legitimate fund company to get the end-user to accept a meeting.
This is an alarming new development: Phishing tactics may now be used by legitimate companies looking to gin up business in improper ways.
Who is the Attacker?
The company at the core of our findings is PERA LLC, based out of Nevada. The company takes over the names of various Public Employees Retirement Association companies and takes advantage of the goodwill of those companies to present an unearned legitimacy for PERA LLC.
Even the registered name of this company is an impersonation attack against Colorado PERA, a respected and long-standing pension fund. And indeed Colorado PERA filed a lawsuit against PERA LLC for “soliciting Colorado’s public employees under false pretenses and misrepresenting that third-party investment representatives are approved by PERA or the PERA employee, when they are not.”
The most recent court records indicate that due to COVID-19, this case has been postponed. This allows PERA LLC to continue to further entrap more unsuspecting teachers and civil servants into joining their deceptive pension fund.
How the Attack Works
The campaigns use all the methods you would expect from a well organized phishing/spam campaign—spoofing the sender in the email header to impersonate an email from the organization; rotating domains and links; rotating the sending IP addresses; and changing the subjects and bodies of the emails themselves.
In the last 30 days, we have seen 39,433 emails from PERA LLC through one of their various domains:
|
Domain
|
Count
|
|
districtadvice.com
|
6,885
|
|
yourretiring.com
|
5,732
|
|
peraexplores.com
|
4,709
|
|
perahelps.com
|
2,999
|
|
pension-analysis.com
|
2,687
|
|
my403bonline.com
|
2,667
|
|
perasolution.com
|
2,292
|
|
peraappointments.com
|
1,932
|
|
pensioninitiative.com
|
1,862
|
|
teacherretirementreviews.com
|
1,442
|
|
aneasyretirement.com
|
976
|
|
peraguides.com
|
893
|
|
employeefinances.com
|
654
|
|
peraprotects.com
|
628
|
|
educatorsavingsnews.com
|
557
|
|
pensionrx.com
|
487
|
|
employeeinsuranceassistance.com
|
468
|
|
district-benefits.com
|
460
|
|
settingaside.com
|
361
|
|
pension-partners.com
|
334
|
|
yourretirementreview.com
|
258
|
|
district-advisor.com
|
150
|
The subject line varies, but here are the most commonly used ones:
|
Assistance for [SCHOOL NAME] Schools Personnel
|
|
Information on State Retirement for [GOVT ORG NAME]
|
|
State Retirement Help for [SCHOOL NAME]
|
|
State Retirement Assistance for [SCHOOL NAME] Personnel
|
|
Retirement Review for [GOVT ORG NAME] Employees
|
Here’s an example of the body of one of the phishing emails:

Once the user clicks the “Set Appointment” button, they are taken to this pre-filled page:
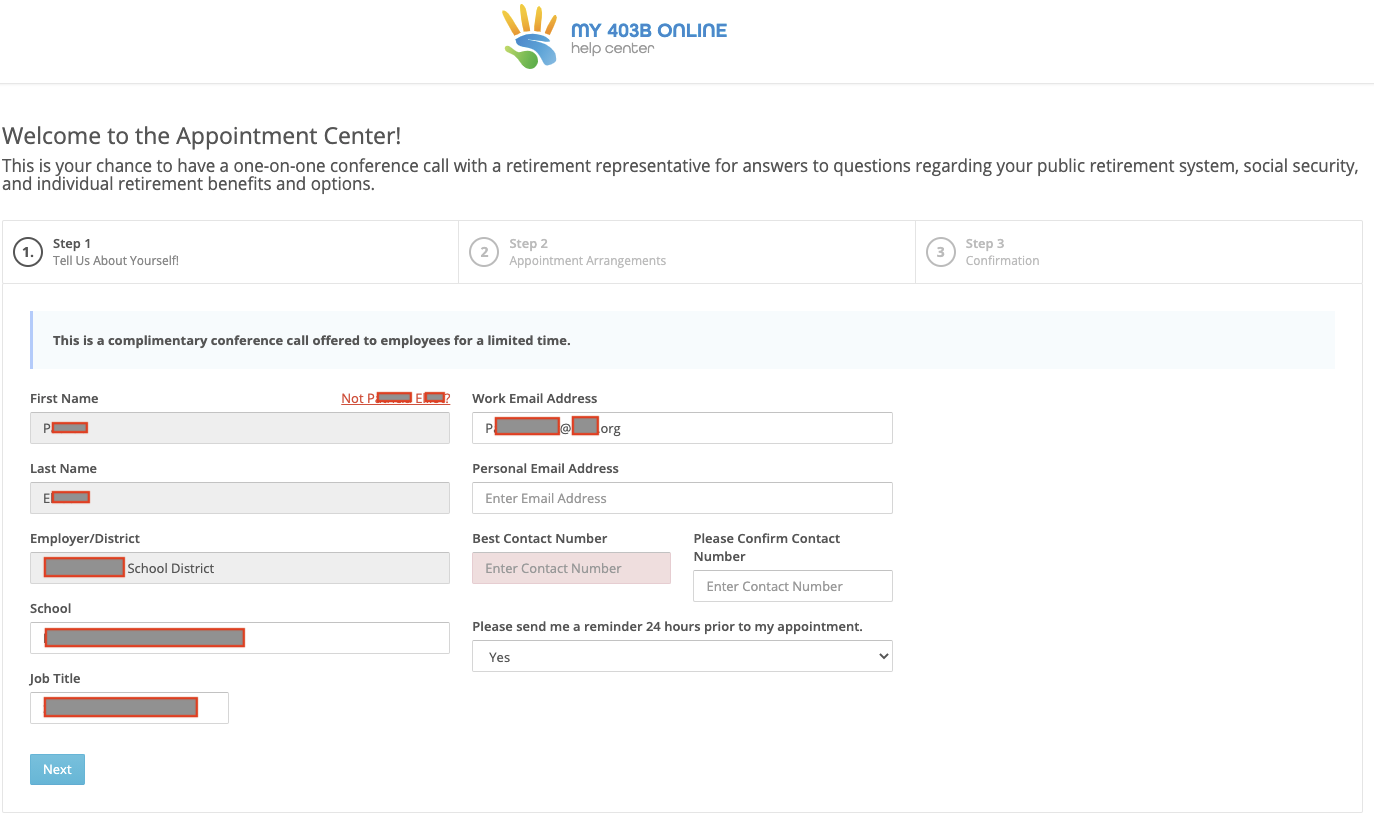
The next page goes to an appointment selecter that looks very similar to most business appointment schedulers.
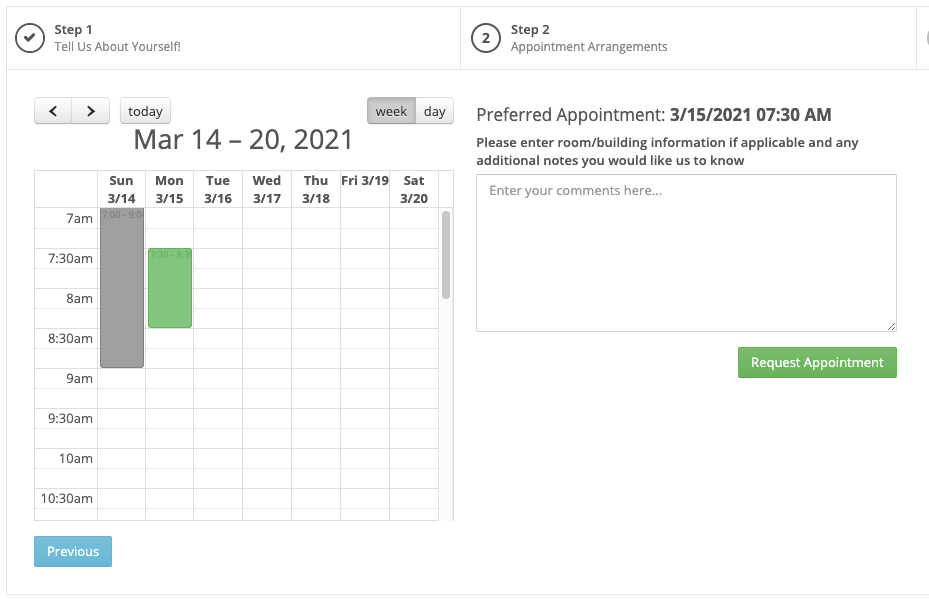
Once everything is completed, the victim is presented with this page:

What Did Avanan Do?
These emails were caught by Avanan, marked as “Phishing” and blocked before they reached the end-users. The senders used a known vulnerability in Microsoft’s 365 SPF check, a method that helped Avanan incriminate the attackers. (We plan to expose this method in one of our upcoming blogs.) An actual SPF/DKIM check that Avanan ran failed and Avanan’s anti-phishing was able to confirm the email includes a domain impersonation attack.
Avanan’s Natural Language Processing then analyzed the content of the email and determined that this was related to financial matters and should not be coming from an email address that fails SPF and DKIM checks. The NLP also detected urgency and a call to action, both indicators commonly used in phishing emails. The rotating domains that were linked by the email had low-traffic/low-reputation and were recently registered, making the links themselves suspicious. Finally, the social-graph that calculates the likelihood of phishing based on prior correspondence also scored this email as quite likely to be phishing. In total, Avanan's AI concluded that, based on these indicators, this email is a phishing attack.
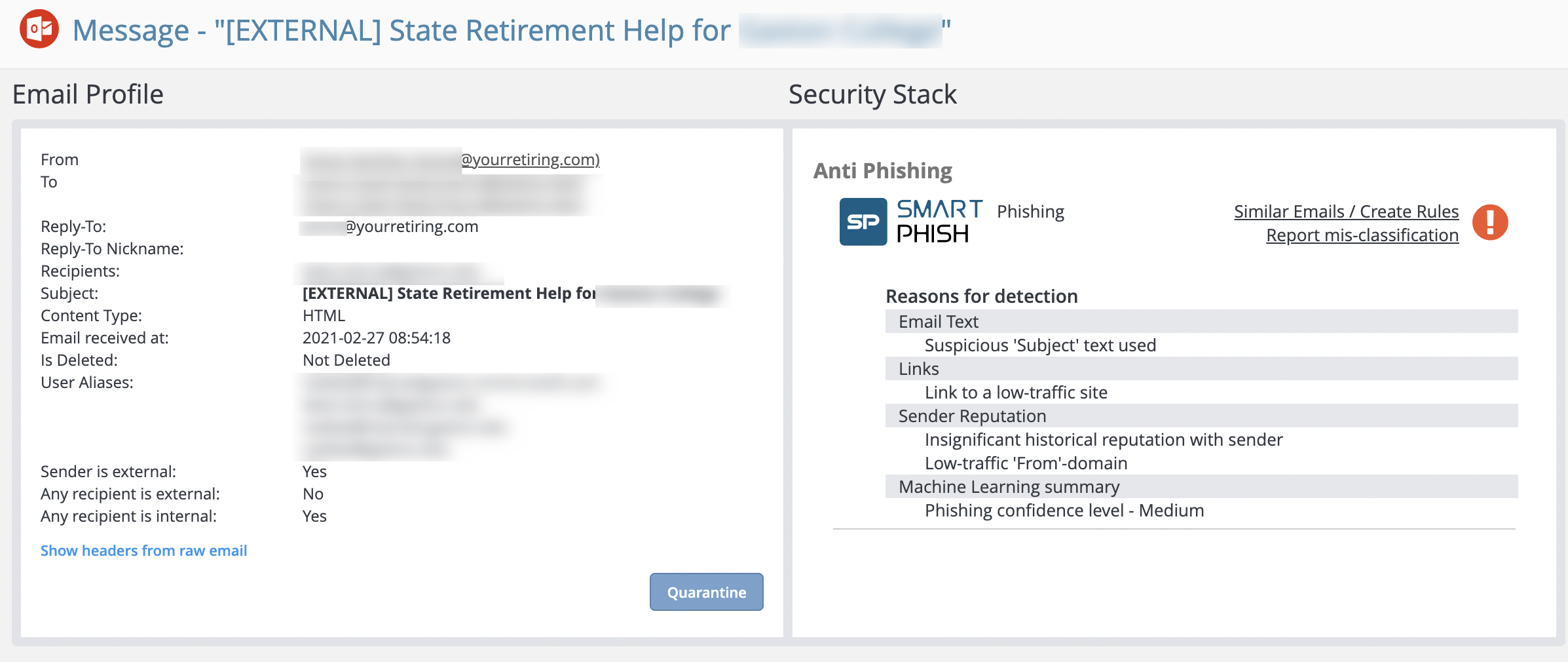
Avanan’s end-users were protected and did not fall victim to this scam, but there are still millions of government and education workers who are seeing these emails delivered to their inboxes every day. Please consider sharing with your employees to warn them of this scam.
As in many other cases, our security analysts “fell victim” on purpose to the attack and scheduled an appointment with a retirement consultant. We will share the experience (and the financial advice we receive) in a follow-up blog.